What are VPN protocols
It is always the VPN protocol that determines how data travels within the VPN network. The most common VPN protocols are:
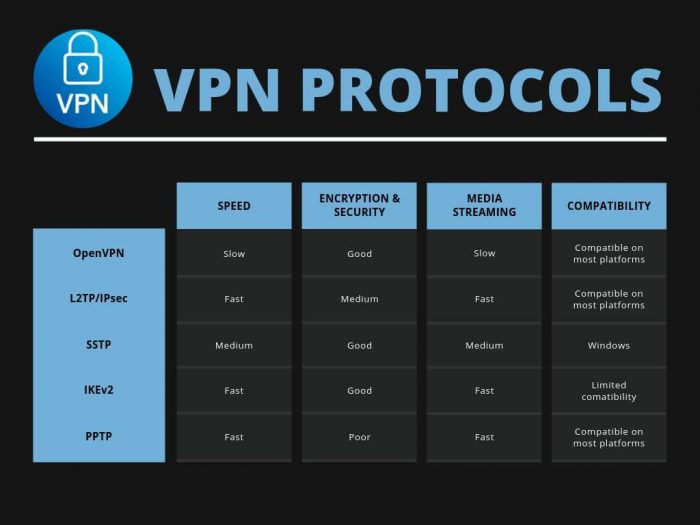
- Point-to-Point Tunnel Protocol (PPTP) – One of the oldest VPN protocols in the world with a distinct advantage: it can be used on virtually any device that exists and is easy to activate on Windows PCs. But that’s where the fun ends.
The level of security is acceptable at best, and this protocol is only used by companies that want to navigate more securely. But for people: skip this protocol, and if the VPN provider only offers PPTP support, ruled out! - L2TP / IPsec (Layer 2 Tunnel Protocol) – Much more secure than PPTP, but not bulletproof. L2TP is a VPN protocol that in its basic design does not use any type of encryption. For this reason, the protocol is always used in conjunction with IPsec to increase security. Also, L2TP uses something called dual encapsulation, so it was well received at launch. The first cabinet establishes a PPP connection to an external host and the second cabinet contains IPsec for extra security.
- SSTP (Secure Socket Tunnel Protocol): Like PPTP, this protocol is also developed by Microsoft. The protocol uses SSL / TLS encryption (a common method to protect web pages) and since both the transmitter and the receiver must approve the transmission, this VPN protocol is considered secure.
- IKEv2: You guessed it! Microsoft is also behind this encryption protocol. IKEv2 is fast and secure and is most commonly used on iOS devices. Because the level of security is very high, this protocol can be used regardless of the device you connect to.
- OpenVPN: the best VPN protocol in the world in terms of speed and level of security. With open source, hundreds of volunteers can also improve their safety and performance with each passing year. And because it is open source, we can be sure that the protocol does not contain nasty back doors or the like.
- WireGuard: a lightweight and flexible protocol for the future. It is predicted that it will take the throne after OpenVPN, but it is not fully developed yet, and until that happens, we must stay away.
In summary, the OpenVPN and IKEv2 protocols should be considered the most secure. The other protocols mentioned above should only be used if you have no other choice.
AES 256: The industry standard for encryption and can, for example, be used with the OpenVPN protocol. According to many, the AES 256 is the best and most efficient encryption standard, and that is true. Furthermore, the AES 256 standard has never been hacked, so it will also remain for a long time. AES protection is also available as AES 128, which also offers complete protection, although not as strong. AES 512 is in development but will not appear for a few years.
How does encryption really work?
In short, encryption means that we put an extra layer of security on the information that is sent. To give an example:
- We send a message through the web.
- A secret encryption key makes the message unreadable to unauthorized people.
- The message is sent (no one has any idea what the message contains).
- Finally, the same message can be unlocked and read by a recipient with the correct password.
On VPN connections, what we already know is the AES encryption that is applied. All the major VPN providers offer AES 256 encryption, and they are all high performance and security options.
Read more: surge in VPN-use during Corona pandemic
Registration policy
The level of security that a VPN provider can offer depends largely on what types of logs it keeps. For example, VPN companies can store:
- Connection logs: informs them what time we connect and from what specific VPN server.
- Information on how many devices we use at the same time: harmless.
- Payment records: They are always encrypted and cannot be used to track us.
- Email Logs – These are also encrypted and cannot be used to find out who we are. However, sign up with an anonymous email address can make you safe as well.
- IP addresses: Although they are also encrypted and generally cannot be used to track us, alarms start to sound. From a theoretical point of view, they can discover who we are by saving this type of information.
- Traffic logs: describes exactly what we do on the web. Generally, only free VPNs keep this type of logs.
In general, the general rule says: the fewer records you keep, the better.
Full transparency is preferred
Outside security companies can examine the top performing VPN providers. These checks, among other things, the source code, the servers and, in short, that the company is behaving correctly.
Does a VPN service make us completely impossible to track online?
Short answer?
No, but almost.
Long answer?
Without a VPN connection, anyone curious can see what we do online. A person with the correct access or some digital tools can take a closer look at everything we left behind on the Internet.
If, instead, we use a VPN service, all Internet traffic is encrypted and, therefore, it is almost impossible for them to intercept our tracks.
Take a look at the following factors before fully deciding:
- Does the VPN provider keep any logs? If so, which ones?
- How is payment information encrypted?
- Are the encryption and security protocols strong enough?
Ultimately, and as you have surely understood, not all VPN companies are equally good or safe to protect us online.