In estimation,1.5 billion people around the globe are using some VPN service to communicate more securely on the internet. But, as cybercriminals are taking an innovative approach to their attacks, the situation calls for developing new, more secure VPN technology.
In this article, we shall explore the latest developments in VPN protocols and how they cater to modern internet and data security problems:
What is a VPN?
Simply put, “A VPN is essentially used to set up secure and encrypted connections between a system within LAN and some other remote system or server.” This helps both entities communicate more securely, as their connection is encrypted.
But then…what is a VPN protocol?
A VPN protocol helps the virtual private network manage this secure communication! It handles authentication, encryption, data transmission, and response. It helps to establish an encrypted tunnel that transmits your data securely to a VPN server.
Now, no one VPN protocol is working to keep the entire internet secure. Still, different protocols prioritize speed, security, multi-device compatibility, etc., and cater to various customer needs.
Why do we need a VPN protocol?
VPN protocols are crucial to establishing safer connections when communicating with remote servers over the Internet. And with new cyber security threats emerging almost every other day, the need for secure protocols becomes more apparent. Here are a few reasons you need one:
- It creates a secure tunnel for your data to travel through without the risk of unauthorized surveillance.
- It encrypts data before transmission to ensure a malicious attacker does not intercept it.
- It authenticates the identity of the systems and servers involved in the communication.
- It ensures data integrity by preventing any source from altering the data.
- It caters to user needs like speed, compatibility, security, etc.
Choosing the suitable VPN protocol
Choosing the suitable VPN protocol is just as essential because depending on your need, the protocol you require would differ. Here is a simplified breakdown of VPN protocols you could use for different purposes:
| Use Case | VPN protocol |
| General security | OpenVPN, IKEv2/IPsec |
| Stable connections | IKEv2/IPsec |
| Low latency gaming | WireGuard, IKEv2/IPsec |
| Fast speed | WireGuard, IKEv2/IPsec |
| Balanced speed and security | IKEv2/IPsec, OpenVPN |
VPN protocols: A brief history of networking
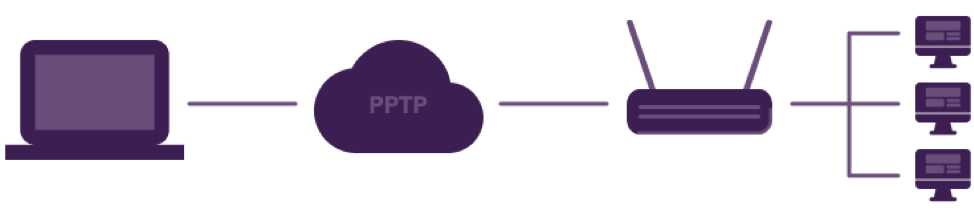
Microsoft created the first widely known VPN protocol in a joint venture with other technological companies in the 1990s, by the name of Point-to-Point Tunneling Protocol or PPTP. The idea behind this venture was to create a solution for safer dial-up connections.
However, several vulnerabilities were discovered in PPTP, and this paved the way for more advanced and secure protocols to emerge. Now we have new protocols like WireGuard that cater to security and gaming speeds or OpenVPN for flexibility and strong security. Even quantum-technology-based protocols are emerging with recent security developments.
5 Emerging Development of New VPN Protocols
1. WireGuard
WireGuard is an emerging VPN protocol that focuses on modern cryptography and was developed in 2018 by Jason A. Donenfeld. It is known for its simplicity, speed, and resilience against potential vulnerabilities.
The protocol uses symmetric encryption algorithms like ChaCha20 for encryption and Poly1305 for message authentication.
It addresses several limitations of traditional protocols like latency, performance overhead, and configuration complexity. WireGuard’s cross-platform support, low latency, and dynamic routing also make it a fast and user-friendly option for gaming.
2. OpenVPN
While OpenVPN is not as recent of discovery as Wireguard, it has been a great help nonetheless when it comes to encryption security and reliability!
It is a highly flexible protocol that is used in various configurations point-to-point, site-to-site, and even for remote access VPNs.It uses TLS with SSL/TLS for key exchange and authentication.
It also supports several encryption algorithms, including AES encryption, Blowfish, Camellia, etc., which makes it adaptable to different security requirements.
3. IKEv2/IPSec
Hybrid protocols have become very popular recently as they combine the advantages of two separate VPN protocols to develop a more efficient product. IKEv2 (Internet Key Exchange version 2) is often combined with IPSec (Internet Protocol Security) to cater to the need for more secure protocols and mobility support.
If you need to switch between different networks, attain stable connectivity, or want low latency for gaming, the IKEv2/IPSec combo is the way to go!
4. QUIC
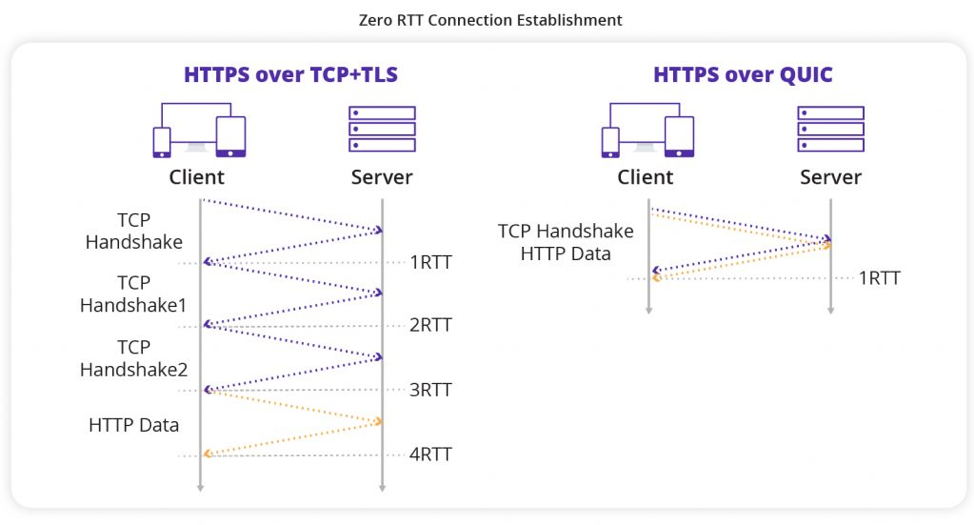
Developed in 2012 by Google, QUIC (Quick UDP Internet Connections) was initially aimed to reduce webpage loading time and provide better security via encryption. It uses UDP to establish faster connectivity and streams multiple data streams simultaneously using multiplexing.
The VPN protocol can also adapt well to changing network conditions and became the foundation for the HTTP/3 protocol. Due to its low latency, QUIC can be used for real-time video conferencing, online gaming, and faster browsing.
5. Quantum-based protocols
After the emergence of Quantum technology, experts have focused on developing more advanced VPN protocols to resist attacks from a Quantum computer. This has led to the development of post-quantum cryptography (PQC), Quantum-Resistant encryption keys, and Quantum-based protocols.
We have limited time before a stable Quantum computer; all realism breaks loose! We need to leverage Quantum mechanics and modern cryptography to deploy more Quantum-safe VPNs to protect data against future threats.
Security, Technology and VPN Protocols go hand-in-hand…
With recent advancements in technology and the emergence of generative AI, Internet security has become a point of concern for many. Cybercriminals are using these technologies to develop more sophisticated cyber attacks.
Under these circumstances, we need more secure VPN protocols and encryption technologies to protect our data during rest and in transit. Advanced protocols WireGuard, QUIC, and Quantum-safe VPNs help protect sensitive information against unauthorized interception and allow users to communicate freely and securely.
Author Bio:
Anas Hassan is a tech geek and cybersecurity enthusiast at PureVPN. He has vast experience in the field of digital transformation industry. When Anas isn’t blogging, he watches the football games.